Some of the likelihood scenarios are the following:

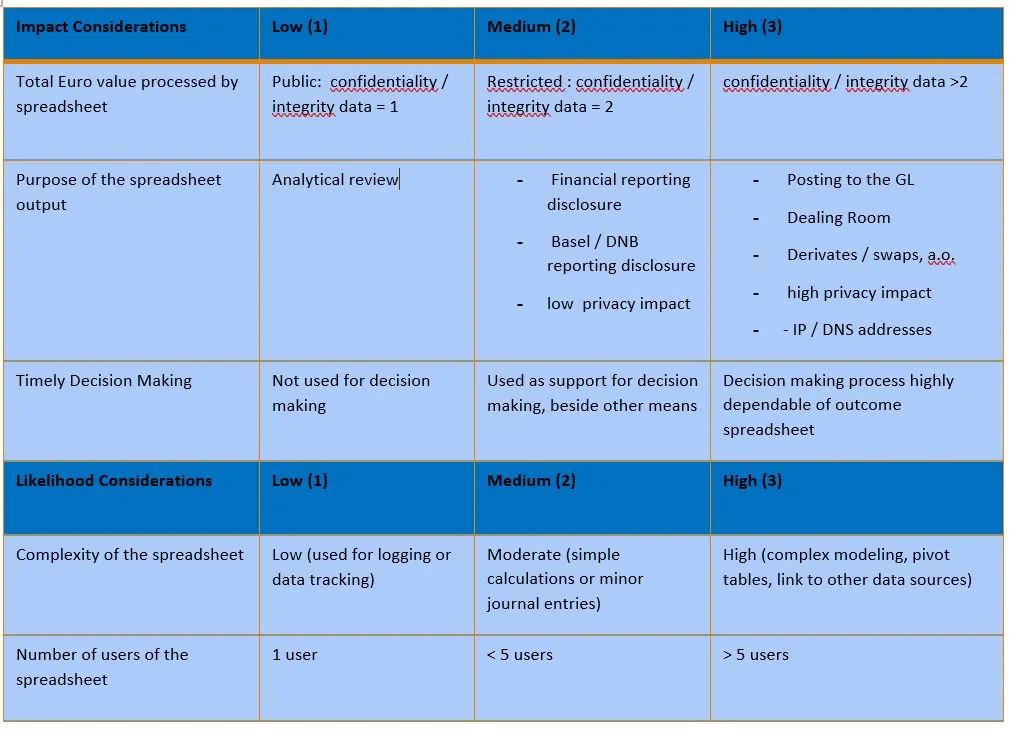
If we classified the confidentiality and integrity rating on a scale of 1-3 , where low =1 and high = 3.
The following overview can be an example:
Typical security measurements to consider are the following:
1. Access control: Storage centrally (dedicated drive or share)
2. Change control: Version control and justify on additional tab
3. Documentation: up to date to understand the business objective and specific functions of the spreadsheet
4. Testing: Formally test the spreadsheet by expericenced 3rd party which will confirm that the spreadsheet processing and related output is functioning as intended
5. Logic inspection: inspect the spreadsheets’ logic. Document this review formally (could be same 3rd party as mentioned above)
6. Input control: Reconcile data inputs to source documents
7. Security an integrity of data: “locking” or protecting sensitive cells, such as formulas and master data.